Yes. We send the real IP address in the x-forwarded-for field. However, some servers require a little tweaking to x-forwarded-for field.
Your web server must be able to read X-Forwarded-For headers. Some web servers, such as LiteSpeed, NGINX and IIS support such a feature by default, while you have to use a module, such as mod_rpaf or mod_remoteip if you're running Apache. The first part of this tutorial will show you how to install and configure Apache with mod_remoteip. We're not going to use mod_rpaf in this example, because it doesn't properly work with CIDRs (IP ranges).
CentOS/RHEL + Apache
1.) Install required packages:
# yum install gcc wget httpd-devel
2.) Download sources:
# wget -O /usr/local/src/mod_remoteip.c https://raw.github.com/ttkzw/mod_remoteip-httpd22/master/mod_remoteip.c
3.) Compile source:
# cd /usr/local/src/
# apxs -i -c -n mod_remoteip.so mod_remoteip.c
4.) Configure:
Create the file /etc/httpd/conf.d/mod_remoteip.conf and paste the following content into it:
LoadModule remoteip_module modules/mod_remoteip.so
RemoteIPHeader X-Forwarded-For
RemoteIPTrustedProxy 199.91.125.0/24
RemoteIPTrustedProxy 199.245.52.0/24
RemoteIPTrustedProxy 199.91.124.0/24
RemoteIPTrustedProxy 185.8.196.130
RemoteIPTrustedProxy 185.8.196.128/25
RemoteIPTrustedProxy 5.254.100.32/27
RemoteIPTrustedProxy 93.115.83.64/26
RemoteIPTrustedProxy 162.222.212.0/24
Save it and exit.
Important: For cPanel servers you should paste the configuration into /usr/local/apache/conf/includes/pre_main_global.conf
6.) Restart Apache:
# service httpd restart
Ubuntu/Debian + Apache
1.) Install required packages:
# apt-get install gcc wget apache2-prefork-dev
2.) Download Sources:
# wget -O /usr/local/src/mod_remoteip.c https://raw.github.com/ttkzw/mod_remoteip-httpd22/master/mod_remoteip.c
3.) Compile source:
# cd /usr/local/src/
# apxs2 -i -c -n mod_remoteip.so mod_remoteip.c
Note: If "apxs2" doesn't work, try "apxs".
4.) Configure:
Create the file /etc/apache2/conf.d/mod_remoteip.conf and paste the following content into it:
LoadModule remoteip_module modules/mod_remoteip.so
RemoteIPHeader X-Forwarded-For
RemoteIPTrustedProxy 209.141.32.0/19
RemoteIPTrustedProxy 198.251.80.0/20
RemoteIPTrustedProxy 185.8.196.0/24
RemoteIPTrustedProxy 185.8.197.0/24
RemoteIPTrustedProxy 5.254.102.128/25
RemoteIPTrustedProxy 5.254.103.128/28
Save it and exit.
6.) Copy module and restart Apache:
# mkdir -p /etc/apache2/modules
# cp /usr/lib/apache2/modules/mod_remoteip.so /etc/apache2/modules/
# service apache2 restart
LiteSpeed
Go to Configuration -> Server, click "Edit" at the "General Settings" box and set "Use Client IP in Header" to "Yes".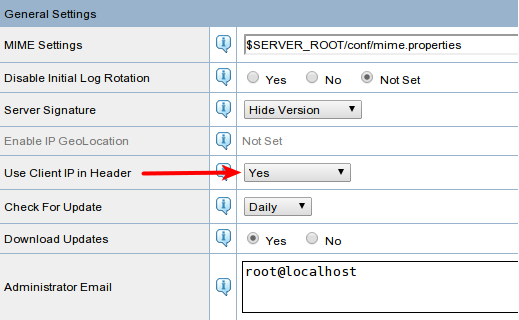
NGINX
Open your main NGINX configuration, which includes the "http" block (most likely /etc/nginx/nginx.conf) and append the "http" block to look as follows:
http {
...
set_real_ip_from 209.141.32.0/19;
set_real_ip_from 198.251.80.0/20;
set_real_ip_from 185.8.196.0/24;
set_real_ip_from 185.8.197.0/24;
set_real_ip_from 5.254.102.128/25;
real_ip_header X-Forwarded-For;
...
}
Restart NGINX - done.


































